| page_type | languages | products | description | urlFragment | ||
|---|---|---|---|---|---|---|
sample |
|
|
This simple sample demonstrates how to use the Microsoft Authentication Library (MSAL) for .NET to get an access token and call an API secured by Azure AD B2C. |
active-directory-b2c-dotnet-desktop |
This branch is using MSAL.NET 4.x. If you are interested in a previous version of the sample using MSAL.NET 2.x, go to the master branch
This simple sample demonstrates how to use the Microsoft Authentication Library (MSAL) for .NET to get an access token and call an API secured by Azure AD B2C.
There are two ways to run this sample:
- Using the demo environment - The sample is already configured to use a demo environment and can be run simply by downloading this repository and running the app on your machine. See steps below for Running with demo environment.
- Using your own Azure AD B2C tenant - If you would like to use your own Azure AD B2C configuration, follow the steps listed below for Using your own Azure AD B2C tenant. Please note, the api call will only work with domains using
{tenantName}.b2clogin.com, as the node.js api used for the api call has been updated to handleb2clogin.comand notlogin.microsoftonline.com. If usinglogin.microsoftonline.comor a custom b2c domain, you will need to host your own web api (see step 3 below), otherwise, you will see "authorized" when making the api call with this sample as-is.
This sample demonstrates how to sign in or sign up for an account at "Wingtip Toys" (the demo environment for this sample) using a WPF Desktop application.
Once signed-in, clicking on the Call API button shows the display name you used when you created your account. The Edit Profile button allows you to change your display name and city. The Logout button logs you out of the application.
From your shell or command line:
git clone https://github.com/Azure-Samples/active-directory-b2c-dotnet-desktop.git
Open the active-directory-b2c-wpf.sln and run the project.
The sample demonstrates the following functionality:
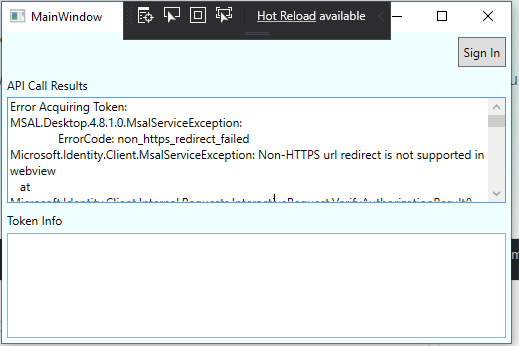
- Click the sign-in button at the top of the application screen. The sample works exactly in the same way regardless of the account type you choose, apart from some visual differences in the authentication and consent experience. Upon successful sign in, the application screen will list some basic profile info for the authenticated user and show buttons that allow you to edit your profile, call an API and sign out.
- Close the application and reopen it. You will see that the app retains access to the API and retrieves the user info right away, without the need to sign in again.
- Sign out by clicking the Sign out button and confirm that you lose access to the API until the exit interactive sign in.
In the previous section, you learned how to run the sample application using the demo environment. In this section, you'll learn how to configure this WPF application and a related Node.js Web API with Azure AD B2C sample to work with your own Azure AD B2C Tenant.
First, you'll need an Azure AD B2C tenant. If you don't have an existing Azure AD B2C tenant that you can use for testing purposes, you can create your own by following these instruction.
This sample uses three types of policies: a unified sign-up/sign-in policy, a profile editing policy, and a password reset policy. Create one policy of each type by following the built-in policy instructions. You may choose to include as many or as few identity providers as you wish.
If you already have existing policies in your Azure AD B2C tenant, feel free to re-use those policies in this sample.
As you saw in the demo environment, this sample calls a Web API at https://fabrikamb2chello.azurewebsites.net. This demo Web API uses the same code found in the sample Node.js Web API with Azure AD B2C, in case you need to reference it for debugging purposes.
You must replace the demo environment Web API with your own Web API. If you do not have your own Web API, you can clone the Node.js Web API with Azure AD B2C sample and register it with your tenant.
First, clone the Node.js Web API sample repository into its own directory, for example:
cd ..
git clone https://github.com/Azure-Samples/active-directory-b2c-javascript-nodejs-webapi.git
Second, follow the instructions at register a Web API with Azure AD B2C to register the Node.js Web API sample with your tenant. Registering your Web API allows you to define the scopes that your single page application will request access tokens for.
Provide the following values for the Node.js Web API registration:
- Provide a descriptive Name for the Node.js Web API, for example,
My Test Node.js Web API. You will identify this application by its Name whenever working in the Azure portal. - Mark Yes for the Web App/Web API setting for your application.
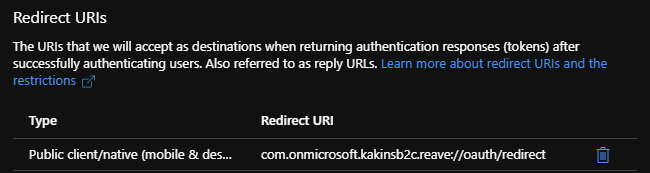
- Set the Reply URL to
http://localhost:5000. This is the port number that the Node.js Web API sample is configured to run on. - Set the AppID URI to
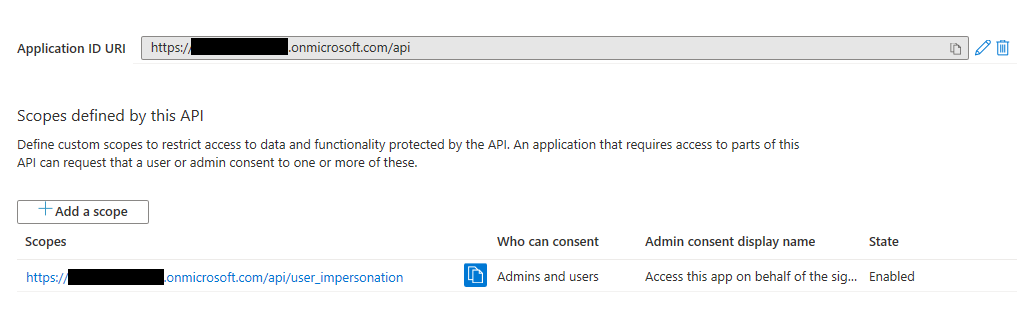
demoapi. This AppID URI is a unique identifier representing this Node.jS Web API. The AppID URI is used to construct the scopes that are configured in you single page application's code. For example, in this Node.js Web API sample, the scope will have the valuehttps://<your-tenant-name>.onmicrosoft.com/demoapi/demo.read - Create the application.
- Once the application is created, open your
My Test Node.js Web APIapplication and then open the Published Scopes window (in the left nav menu) and add the scopedemo.readfollowed by a descriptiondemoing a read scenario. Click Save.
Third, in the index.html file of the Node.js Web API sample, update the following variables to refer to your Web API registration.
var tenantID = "<your-tenant-name>.onmicrosoft.com";
var clientID = "<Application ID for your Node.js Web API - found on Properties page in Azure portal>";
var policyName = "<Name of your sign in / sign up policy, e.g. B2C_1_SiUpIn>";
Lastly, to run your Node.js Web API, run the following command from your shell or command line
npm install && npm update
node index.js
Your Node.js Web API sample is now running on Port 5000.
Now you need to register your native app in your B2C tenant, so that it has its own Application ID.
Your native application registration should include the following information:
- Provide a descriptive Name for the single page application, for example,
My Test WPF App. You will identify this application by its Name within the Azure portal. - Mark Yes for the Native Client setting for your application.
- Create your application.
- Once the application is created, open your
My Test WPF Appand open the API Access window (in the left nav menu). Click Add and select the name of the Node.js Web API you registered previously, for exampleMy Test Node.js Web API. Select the scope(s) you defined previously, for example,demo.readand hit Save.
- Open the solution in Visual Studio.
- Open the
App.xaml.csfile. - Find the assignment for
public static string Tenantand replace the value with your tenant name. - Find the assignment for
public static string ClientIDand replace the value with the Application ID from your Native app registration, for exampleMy Test WPF App. - Find the assignment for each of the policies, for example
public static string PolicySignUpSignIn, and replace the names of the policies you created in Step 2, e.g.b2c_1_SiUpIn - Find the assignment for the scopes
public static string[] ApiScopesand replace with the scope you created in Step 3, for example,https://<your-tenant-name>.onmicrosoft.com/demoapi/demo.read. - Change the
ApiEndpointvariable to point to your Node.js Web APIhelloendpoint running locally at"http://localhost:5000/hello"
- Rebuild the solution and run the app.
- Click the sign-in button at the top of the application screen. The sample works exactly in the same way regardless of the account type you choose, apart from some visual differences in the authentication and consent experience. Upon successful sign in, the application screen will list some basic profile info for the authenticated user and show buttons that allow you to edit your profile, call an API and sign out.
- Close the application and reopen it. You will see that the app retains access to the API and retrieves the user info right away, without the need to sign in again.
- Sign out by clicking the Sign out button and confirm that you lose access to the API until the exit interactive sign in.
For more information on Azure B2C, see the Azure AD B2C documentation homepage.