Permify is on the lookout for engineers eager to tackle challenges in authorization. Join us!
Permify is a open-source authorization service for creating and managing fine-grained permissions in your applications and services. Inspired by Google’s consistent, global authorization system, Google Zanzibar
Our goal is to make Google's Zanzibar available to everyone and help them build robust, flexible, and easily auditable authorization systems that perform well in scaled environments.
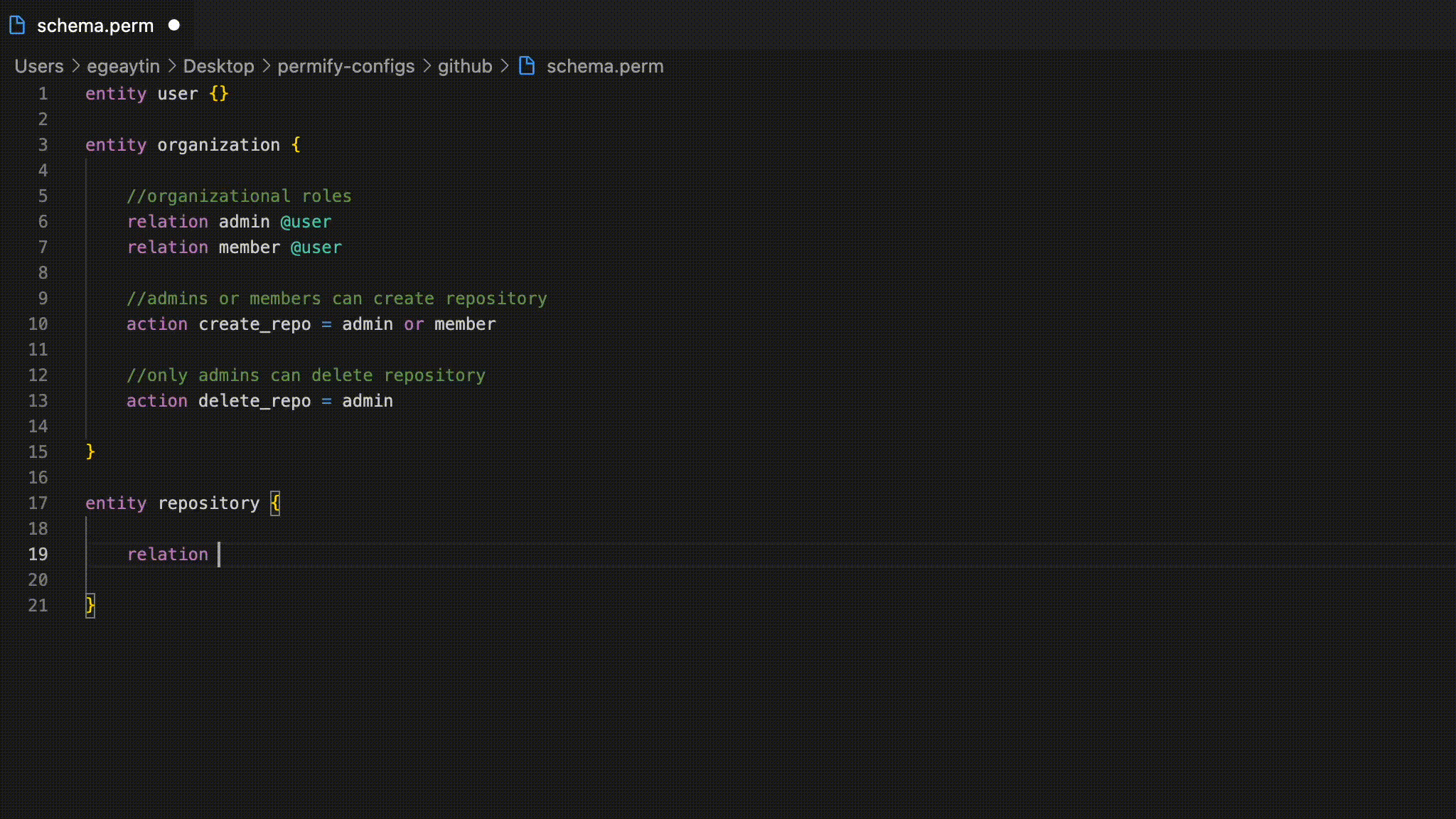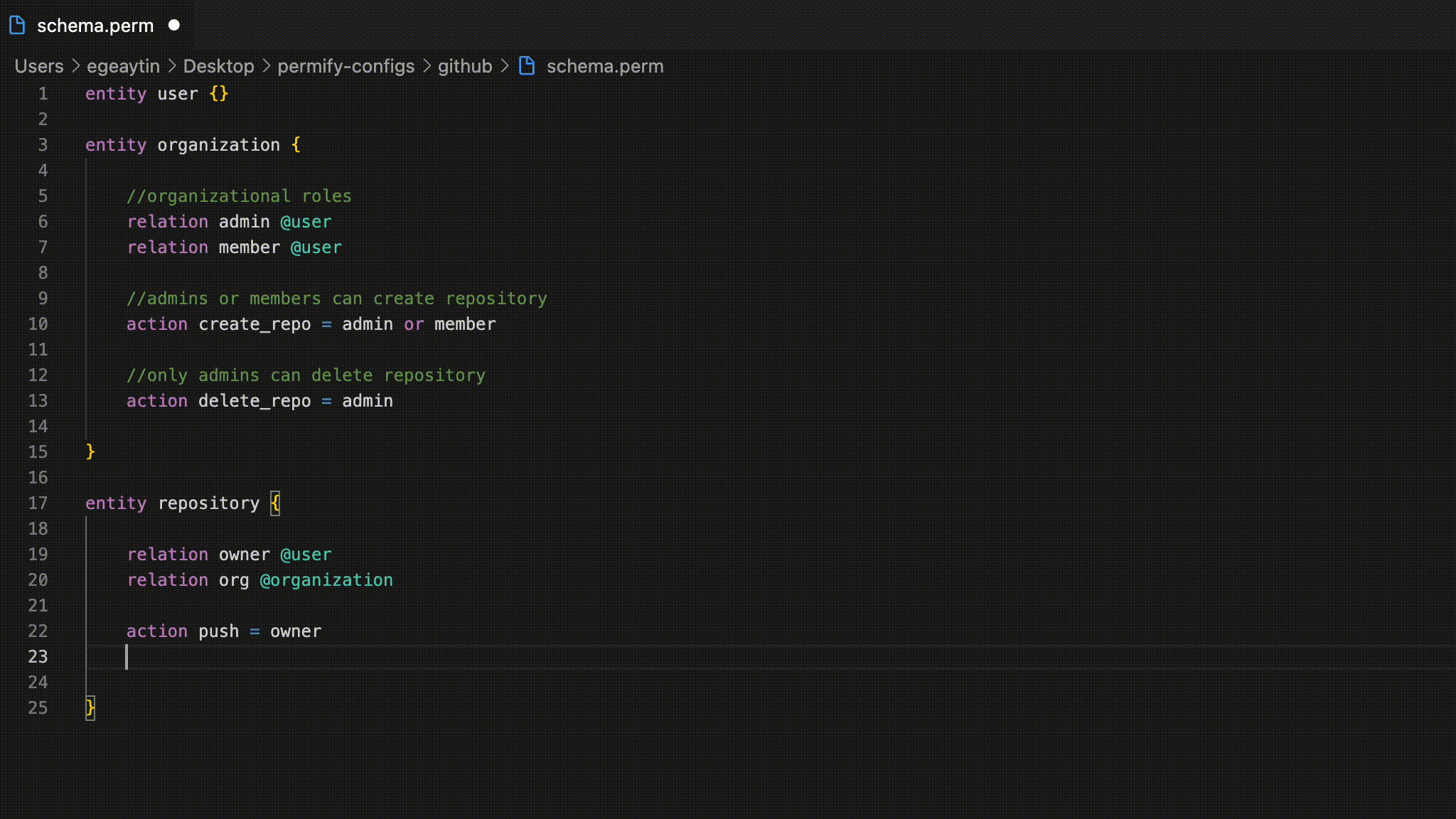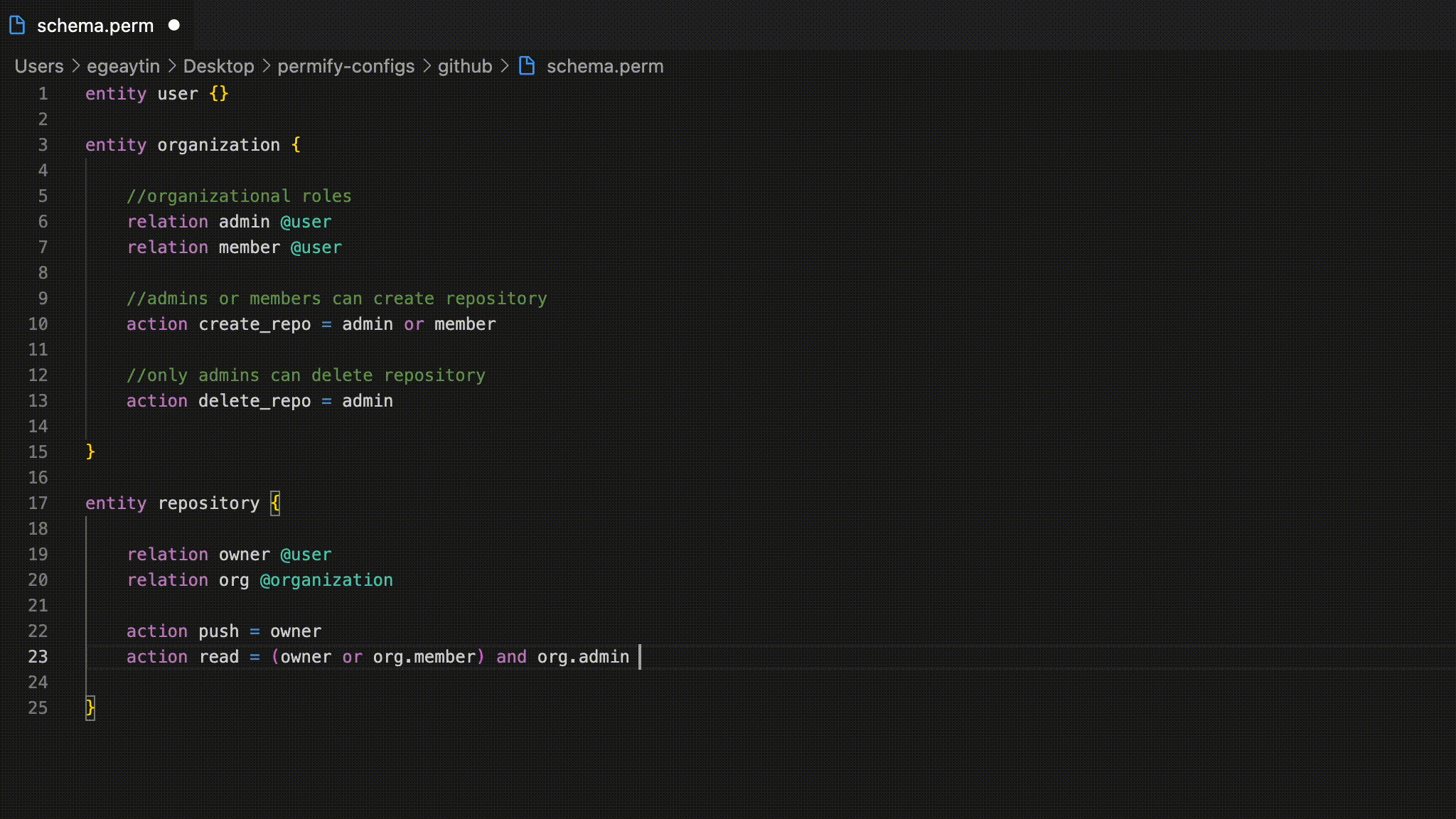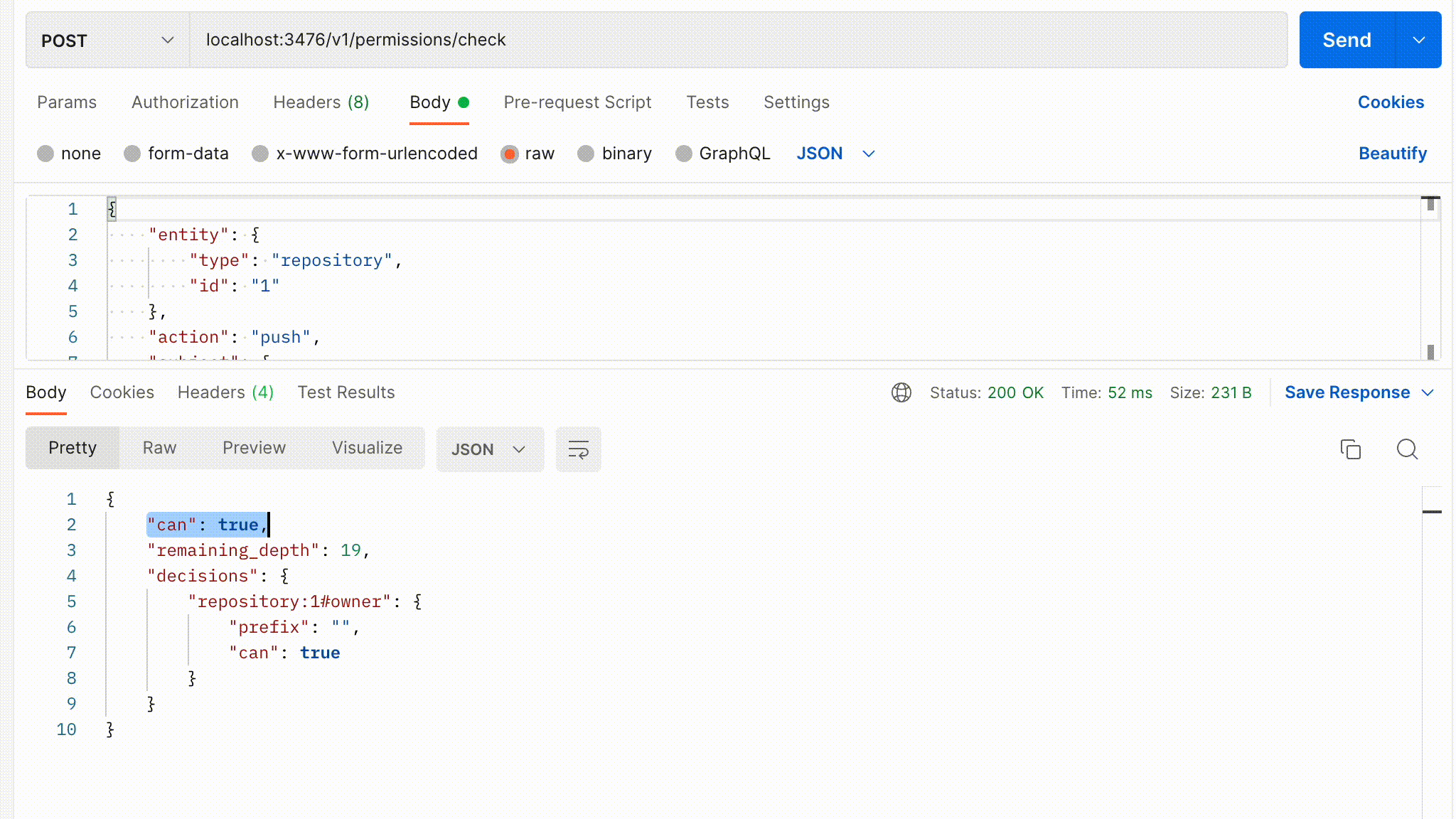
🔮 Create permissions and policies using Permify's flexible authorization language that is compatible with traditional roles and permissions (RBAC), arbitrary relations between users and objects (ReBAC), and attributes (ABAC).
🔐 Manage and store authorization data in your preferred database with high availability and consistency.
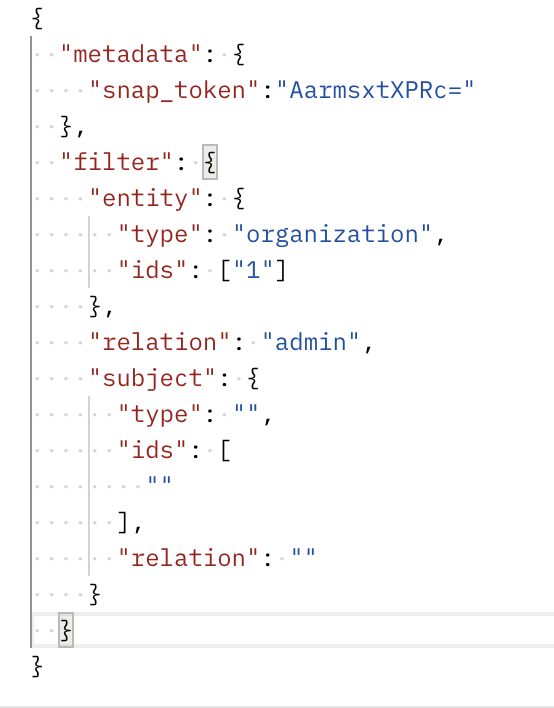
✅ Interact with the Permify API to perform access checks, filter your resources with specific permissions, perform bulk permission checks for various resources, and more.
🧪 Test your authorization logic with Permify's schema testing. You can conduct scenario-based testing, policy coverage analysis, and IDL parser integration to achieve end-to-end validations for your desired authorization schema.
⚙️ Create custom and isolated authorization models for different applications using Permify Multi-Tenancy support, all managed within a single place, Permify instance.
- Follow a guide to model your authorization using Permify's Authorization Language.
- See our Playground, build your authorization logic and test it with sample data.
- Explore overview of Permify API and learn how to interact with it.
- See our article to examine Google Zanzibar in a nutshell.
You can quickly start Permify on your local with running the docker command below:
docker run -p 3476:3476 -p 3478:3478 ghcr.io/permify/permify serveThis will start Permify with the default configuration options:
- Port 3476 is used to serve the REST API.
- Port 3478 is used to serve the GRPC Service.
- Authorization data stored in memory.
See all of the options that you can use to set up and deploy Permify in your servers.
You can test your connection with creating an GET request,
localhost:3476/healthzWe would love to hear from you!
Get the latest product updates, receive immediate assistance from our team members, and feel free to ask any questions about Permify or authorization in a broader context by joining our conversation on Discord!
The open source community thrives on contributions, offering an incredible space for learning, inspiration, and creation. Your contributions are immensely valued and appreciated!
Here are the ways to contribute to Permify:
- Contribute to codebase: We're collaboratively working with our community to make Permify the best it can be! You can develop new features, fix existing issues or make third-party integrations/packages.
- Improve documentation: Alongside our codebase, documentation one of the most significant part in our open-source journey. We're trying to give the best DX possible to explain ourselves and Permify. And you can help on that with importing resources or adding new ones.
- Contribute to playground: Permify playground allows you to visualize and test your authorization logic. You can contribute to our playground by improving its user interface, fixing glitches, or adding new features.
We have a list of issues where you can contribute and gain bounty award! Bounties will be awarded for fixing issues via accepted Pull Requests (PR).
Before start please see our contributing guide.
You can find Permify's Public Roadmap here!
If you like Permify, please consider giving us a ⭐