I'm having a problem while using the simulation mode on one of our RODCs.
[2023-01-04 10:26:54] : - Contacting DC in AD domain ...[RODC1.<domain>]...
[2023-01-04 10:26:54] : * DC is Reachable...
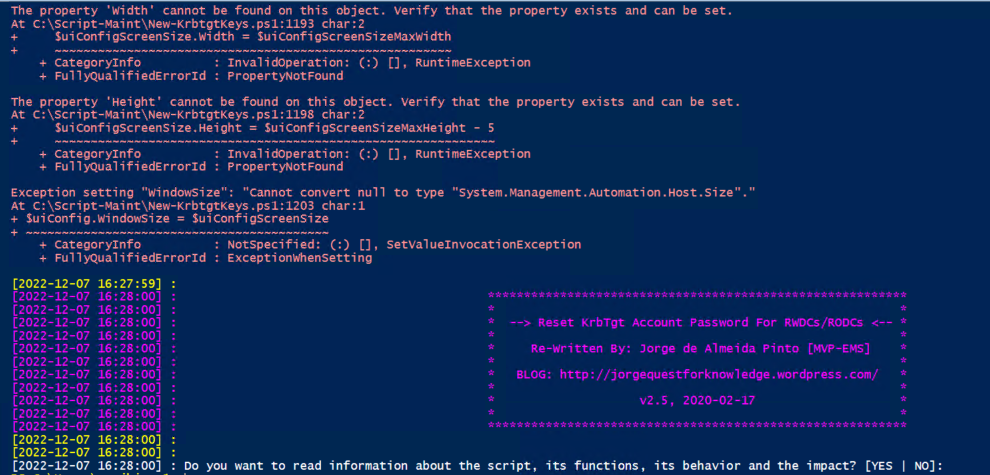
Exception calling "SetInfo" with "0" argument(s): "An operations error occurred.
"
At C:\temp\new-krbtkeys.ps1:591 char:2
+ $rootDSE.SetInfo()
+ ~~~~~~~~~~~~~~~~~~
+ CategoryInfo : NotSpecified: (:) [], MethodInvocationException
+ FullyQualifiedErrorId : CatchFromBaseAdapterMethodInvokeTI
[2023-01-04 10:26:56] : * The new password for Object [CN=krbtgt_19109_TEST,CN=Users,DC=<domain>,DC=local] now does exist in the AD database
Even though the script informs that the password was replicated to the RODC, it, in fact, wasn't (confirmed by manually checking the passwordLastSet attribute).
There's no such problem with the other RODC that we have.
I'm wondering whether this is a no go for using the script on this RODC or, maybe, I can just force the replication manually after using the script and that'll be all.
[2023-01-04 10:25:55] : LOADING REQUIRED POWERSHELL MODULES...
[2023-01-04 10:25:55] :
[2023-01-04 10:25:55] : PoSH Module 'ActiveDirectory' Already Loaded...
[2023-01-04 10:25:55] :
[2023-01-04 10:25:55] : PoSH Module 'GroupPolicy' Already Loaded...
[2023-01-04 10:25:55] :
[2023-01-04 10:25:55] : ------------------------------------------------------------------------------------------------------------------------------------------------------
[2023-01-04 10:25:55] : SELECT THE MODE OF OPERATION...
[2023-01-04 10:25:55] :
[2023-01-04 10:25:55] : Which mode of operation do you want to execute?
[2023-01-04 10:25:55] :
[2023-01-04 10:25:55] : - 1 - Informational Mode (No Changes At All)
[2023-01-04 10:25:55] :
[2023-01-04 10:25:55] : - 2 - Simulation Mode (Temporary Canary Object Created, No Password Reset!)
[2023-01-04 10:25:55] :
[2023-01-04 10:25:55] : - 3 - Simulation Mode - Use KrbTgt TEST/BOGUS Accounts (Password Will Be Reset Once!)
[2023-01-04 10:25:55] :
[2023-01-04 10:25:55] : - 4 - Real Reset Mode - Use KrbTgt PROD/REAL Accounts (Password Will Be Reset Once!)
[2023-01-04 10:25:55] :
[2023-01-04 10:25:55] :
[2023-01-04 10:25:55] : - 8 - Create TEST KrbTgt Accounts
[2023-01-04 10:25:55] : - 9 - Cleanup TEST KrbTgt Accounts
[2023-01-04 10:25:55] :
[2023-01-04 10:25:55] :
[2023-01-04 10:25:55] : - 0 - Exit Script
[2023-01-04 10:25:55] :
[2023-01-04 10:25:55] : Please specify the mode of operation:
[2023-01-04 10:25:57] :
[2023-01-04 10:25:57] : --> Chosen Mode: Mode 3 - Simulation Mode - Use KrbTgt TEST/BOGUS Accounts (Password Will Be Reset Once!)...
[2023-01-04 10:25:57] :
[2023-01-04 10:25:57] : ------------------------------------------------------------------------------------------------------------------------------------------------------
[2023-01-04 10:25:57] : SPECIFY THE TARGET AD FOREST...
[2023-01-04 10:25:57] :
[2023-01-04 10:25:57] : For the AD forest to be targeted, please provide the FQDN or press [ENTER] for the current AD forest:
[2023-01-04 10:26:04] :
[2023-01-04 10:26:04] : --> Selected AD Forest: '<domain>'...
[2023-01-04 10:26:04] :
[2023-01-04 10:26:04] : Checking Resolvability of the specified Local AD forest '<domain>' through DNS...
[2023-01-04 10:26:04] :
[2023-01-04 10:26:04] : The specified Local AD forest '<domain>' is resolvable through DNS!
[2023-01-04 10:26:04] :
[2023-01-04 10:26:04] : Continuing Script...
[2023-01-04 10:26:04] :
[2023-01-04 10:26:04] :
[2023-01-04 10:26:04] : Checking Accessibility of the specified AD forest '<domain>' By Trying To Retrieve AD Forest Data...
[2023-01-04 10:26:04] :
[2023-01-04 10:26:04] : The specified AD forest '<domain>' is accessible!
[2023-01-04 10:26:04] :
[2023-01-04 10:26:04] : Continuing Script...
[2023-01-04 10:26:04] :
[2023-01-04 10:26:04] : ------------------------------------------------------------------------------------------------------------------------------------------------------
[2023-01-04 10:26:04] : SELECT THE TARGET AD DOMAIN...
[2023-01-04 10:26:04] :
[2023-01-04 10:26:04] : Forest Mode/Level...: Windows2008R2Forest
[2023-01-04 10:26:04] :
[2023-01-04 10:26:04] : List Of AD Domains In AD Forest '<domain>'...
[2023-01-04 10:26:04] :
[2023-01-04 10:26:04] :
Name DomainSID IsRootDomain DomainMode IsCurrentDomain IsAvailable PDCFsmoOwner NearestRWDC
---- --------- ------------ ---------- --------------- ----------- ------------ -----------
<domain> S-1-5-21-839615072-2308167561-3032929121 TRUE Windows2008R2Domain TRUE TRUE DC4.<domain> DC4.<domain>
[2023-01-04 10:26:04] : --> Found [1] AD Domain(s) in the AD forest '<domain>'...
[2023-01-04 10:26:04] :
[2023-01-04 10:26:04] : For the AD domain to be targeted, please provide the FQDN or press [ENTER] for the current AD domain:
[2023-01-04 10:26:08] :
[2023-01-04 10:26:08] : --> Selected AD Domain: '<domain>'...
[2023-01-04 10:26:08] :
[2023-01-04 10:26:08] : Checking existence of the specified AD domain '<domain>' in the AD forest '<domain>'...
[2023-01-04 10:26:08] :
[2023-01-04 10:26:08] : The specified AD domain '<domain>' exists in the AD forest '<domain>'!
[2023-01-04 10:26:08] :
[2023-01-04 10:26:08] : Continuing Script...
[2023-01-04 10:26:08] :
[2023-01-04 10:26:08] : ------------------------------------------------------------------------------------------------------------------------------------------------------
[2023-01-04 10:26:08] : TESTING IF REQUIRED PERMISSIONS ARE AVAILABLE (DOMAIN/ENTERPRISE ADMINS OR ADMINISTRATORS CREDENTIALS)...
[2023-01-04 10:26:08] :
[2023-01-04 10:26:08] : The user account '<username>' is running with Domain Administrator equivalent permissions in the AD Domain '<domain>'!...
[2023-01-04 10:26:08] : The user account '<username>' is a member of '<domain>\Domain Admins'!...
[2023-01-04 10:26:08] :
[2023-01-04 10:26:08] : Continuing Script...
[2023-01-04 10:26:08] :
[2023-01-04 10:26:08] : ------------------------------------------------------------------------------------------------------------------------------------------------------
[2023-01-04 10:26:08] : GATHERING TARGETED AD DOMAIN INFORMATION...
[2023-01-04 10:26:08] :
[2023-01-04 10:26:15] : Domain FQDN...........................: '<domain>'
[2023-01-04 10:26:15] : Domain Functional Mode................: 'Windows2008R2Domain'
[2023-01-04 10:26:15] : Domain Functional Mode Level..........: '4'
[2023-01-04 10:26:15] : FQDN RWDC With PDC FSMO...............: 'DC4.<domain>'
[2023-01-04 10:26:15] : DSA RWDC With PDC FSMO................: 'CN=NTDS Settings,CN=DC4,CN=Servers,CN=SiteHQ,CN=Sites,CN=Configuration,DC=<domain>,DC=local'
[2023-01-04 10:26:15] : Max TGT Lifetime (Hours)..............: '10'
[2023-01-04 10:26:15] : Max Clock Skew (Minutes)..............: '5'
[2023-01-04 10:26:15] : TGT Lifetime/Clock Skew Sourced From..: 'Default Domain GPO'
[2023-01-04 10:26:15] :
[2023-01-04 10:26:15] : Checking Domain Functional Mode of targeted AD domain '<domain>' is high enough...
[2023-01-04 10:26:15] :
[2023-01-04 10:26:15] : The specified AD domain '<domain>' has a Domain Functional Mode of 'Windows2008Domain (3)' or higher!...
[2023-01-04 10:26:15] :
[2023-01-04 10:26:15] : Continuing Script...
[2023-01-04 10:26:15] :
[2023-01-04 10:26:15] : ------------------------------------------------------------------------------------------------------------------------------------------------------
[2023-01-04 10:26:15] : GATHERING DOMAIN CONTROLLER INFORMATION AND TESTING CONNECTIVITY...
[2023-01-04 10:26:15] :
[2023-01-04 10:26:16] :
[2023-01-04 10:26:16] : List Of Domain Controllers In AD Domains '<domain>'...
[2023-01-04 10:26:16] :
[2023-01-04 10:26:16] :
Host Name PDC Site Name DS Type Krb Tgt Pwd Last Set Org RWDC Org Time Ver IP Address OS Version Reachable Source RWDC FQDN Source RWDC DSA
--------- --- --------- ------- ------- ------------ -------- -------- --- ---------- ---------- --------- ---------------- ---------------
DC4.<domain> True SiteHQ Read/Write krbtgt_TEST 2023-01-02 12:12:13 DC4.<domain> 2023-01-02 12:12:13 3 10.10.14.154 Windows Server 2022 Datacenter True N.A. N.A.
DC3.<domain> False SiteHQ Read/Write krbtgt_TEST 2023-01-02 12:12:13 DC4.<domain> 2023-01-02 12:12:13 3 10.10.14.153 Windows Server 2022 Datacenter True DC4.<domain> CN=NTDS Settings,CN=DC4,CN=...
DC2.<domain> False SiteHQ Read/Write krbtgt_TEST 2023-01-02 12:12:13 DC4.<domain> 2023-01-02 12:12:13 3 10.0.90.32 Windows Server 2012 Standard True DC4.<domain> CN=NTDS Settings,CN=DC4,CN=...
DC1.<domain> False SiteHQ Read/Write krbtgt_TEST 2023-01-02 12:12:13 DC4.<domain> 2023-01-02 12:12:13 3 10.0.90.31 Windows Server 2012 Standard True DC4.<domain> CN=NTDS Settings,CN=DC4,CN=...
RODC1.<domain> False <Site1> Read-Only krbtgt_19109_TEST 2023-01-03 16:48:05 DC3.<domain> 2023-01-03 16:48:05 4 172.17.18.10 Windows Server 2016 Standard Evaluation True DC3.<domain> CN=NTDS Settings,CN=DC3,CN=...
RODC2.<domain> False <Site2> Read-Only krbtgt_33912_TEST 2023-01-03 16:58:57 DC3.<domain> 2023-01-03 16:58:57 4 10.102.14.20 Windows Server 2016 Standard True DC3.<domain> CN=NTDS Settings,CN=DC3,CN=...
[2023-01-04 10:26:16] :
[2023-01-04 10:26:16] : REMARKS:
[2023-01-04 10:26:16] : - 'N.A.' in the columns 'Source RWDC FQDN' and 'Source RWDC DSA' means the RWDC is considered as the master for this script.
[2023-01-04 10:26:16] : - 'RODC Unreachable' in the columns 'Source RWDC FQDN' and 'Source RWDC DSA' means the RODC cannot be reached to determine its replicating source
[2023-01-04 10:26:16] : RWDC/DSA. The unavailability can be due to firewalls/networking or the RODC actually being down.
[2023-01-04 10:26:16] : - 'Unknown' in various columns means that an RODC was found that may not be a true Windows Server RODC. It may be an appliance acting as an RODC.
[2023-01-04 10:26:16] : - 'RWDC Demoted' in the column 'Org RWDC' means the RWDC existed once, but it does not exist anymore as it has been decommissioned in the past.
[2023-01-04 10:26:16] : This is normal.
[2023-01-04 10:26:16] : - 'No Such Object' in the columns 'Pwd Last Set', 'Org RWDC', 'Org Time' or 'Ver' means the targeted object was not found in the AD domain.
[2023-01-04 10:26:16] : Although this is possible for any targeted object, this is most likely the case when targeting the KrbTgt TEST/BOGUS accounts and if those
[2023-01-04 10:26:16] : do not exist yet. This may also occur for an appliance acting as an RODC as in that case no KrbTgt TEST/BOGUS account is created.
[2023-01-04 10:26:16] :
[2023-01-04 10:26:16] :
[2023-01-04 10:26:16] :
[2023-01-04 10:26:16] : --> Found [6] Real DC(s) In AD Domain...
[2023-01-04 10:26:16] :
[2023-01-04 10:26:16] : --> Found [4] RWDC(s) In AD Domain...
[2023-01-04 10:26:16] : --> Found [4] Reachable RWDC(s) In AD Domain...
[2023-01-04 10:26:16] : --> Found [0] UnReachable RWDC(s) In AD Domain...
[2023-01-04 10:26:16] :
[2023-01-04 10:26:16] : --> Found [2] RODC(s) In AD Domain...
[2023-01-04 10:26:16] : --> Found [2] Reachable RODC(s) In AD Domain...
[2023-01-04 10:26:16] : --> Found [0] UnReachable RODC(s) In AD Domain...
[2023-01-04 10:26:16] : --> Found [0] Undetermined RODC(s) In AD Domain...
[2023-01-04 10:26:16] :
[2023-01-04 10:26:16] : ------------------------------------------------------------------------------------------------------------------------------------------------------
[2023-01-04 10:26:16] : SELECT THE SCOPE OF THE KRBTGT ACCOUNT(S) TO TARGET...
[2023-01-04 10:26:16] :
[2023-01-04 10:26:16] : Which KrbTgt account do you want to target?
[2023-01-04 10:26:16] :
[2023-01-04 10:26:16] : - 1 - Scope of KrbTgt in use by all RWDCs in the AD Domain
[2023-01-04 10:26:16] :
[2023-01-04 10:26:16] : - 2 - Scope of KrbTgt in use by specific RODC - Single RODC in the AD Domain
[2023-01-04 10:26:16] :
[2023-01-04 10:26:16] : - 3 - Scope of KrbTgt in use by specific RODC - Multiple RODCs in the AD Domain
[2023-01-04 10:26:16] :
[2023-01-04 10:26:16] : - 4 - Scope of KrbTgt in use by specific RODC - All RODCs in the AD Domain
[2023-01-04 10:26:16] :
[2023-01-04 10:26:16] :
[2023-01-04 10:26:16] : - 0 - Exit Script
[2023-01-04 10:26:16] :
[2023-01-04 10:26:16] : Please specify the scope of KrbTgt Account to target:
[2023-01-04 10:26:38] :
[2023-01-04 10:26:38] : --> Chosen Scope KrbTgt Account Target: 2 - Scope of KrbTgt in use by specific RODC - Single RODC in the AD Domain...
[2023-01-04 10:26:38] :
[2023-01-04 10:26:38] : Specify the FQDN of single RODC for which the KrbTgt Account Password must be reset:
[2023-01-04 10:26:46] :
[2023-01-04 10:26:46] : --> Specified RODC:
[2023-01-04 10:26:46] : * RODC1.<domain>
[2023-01-04 10:26:46] :
[2023-01-04 10:26:46] : ------------------------------------------------------------------------------------------------------------------------------------------------------
[2023-01-04 10:26:46] : REAL RESET MODE (MODE 3) - RESETTING PASSWORD OF SCOPED KRBTGT ACCOUNT(S) (2 - Scope of KrbTgt in use by specific RODC - Single RODC in the AD Domain...)
[2023-01-04 10:26:46] :
[2023-01-04 10:26:46] : Do you really want to continue and execute 'Mode 3'? [CONTINUE | STOP]:
[2023-01-04 10:26:54] :
[2023-01-04 10:26:54] : --> Chosen: continue
[2023-01-04 10:26:54] :
[2023-01-04 10:26:54] : +++++
[2023-01-04 10:26:54] : +++ Processing KrbTgt Account....: 'krbtgt_19109_TEST' | 'CN=krbtgt_19109_TEST,CN=Users,DC=<domain>,DC=local' +++
[2023-01-04 10:26:54] : +++ Used By RODC.................: 'RODC1.<domain>' (Site: Site1) +++
[2023-01-04 10:26:54] : +++++
[2023-01-04 10:26:54] :
[2023-01-04 10:26:54] : --> RWDC To Reset Password On.............: 'DC3.<domain>'
[2023-01-04 10:26:54] : --> sAMAccountName Of KrbTgt Account......: 'krbtgt_19109_TEST'
[2023-01-04 10:26:54] : --> Distinguished Name Of KrbTgt Account..: 'CN=krbtgt_19109_TEST,CN=Users,DC=<domain>,DC=local'
[2023-01-04 10:26:54] : --> Number Of Chars For Pwd Generation....: '64'
[2023-01-04 10:26:54] :
[2023-01-04 10:26:54] : --> Previous Password Set Date/Time.......: '2023-01-03 16:48:05'
[2023-01-04 10:26:54] : --> New Password Set Date/Time............: '2023-01-04 10:26:54'
[2023-01-04 10:26:54] :
[2023-01-04 10:26:54] : --> Previous Originating RWDC.............: 'DC3.<domain>'
[2023-01-04 10:26:54] : --> New Originating RWDC..................: 'DC3.<domain>'
[2023-01-04 10:26:54] :
[2023-01-04 10:26:54] : --> Previous Originating Time.............: '2023-01-03 16:48:05'
[2023-01-04 10:26:54] : --> New Originating Time..................: '2023-01-04 10:26:54'
[2023-01-04 10:26:54] :
[2023-01-04 10:26:54] : --> Previous Version Of Attribute Value...: '4'
[2023-01-04 10:26:54] : --> New Version Of Attribute Value........: '5'
[2023-01-04 10:26:54] :
[2023-01-04 10:26:54] : --> The new password for [CN=krbtgt_19109_TEST,CN=Users,DC=<domain>,DC=local] HAS BEEN SET on RWDC [DC3.<domain>]!...
[2023-01-04 10:26:54] :
[2023-01-04 10:26:54] :
[2023-01-04 10:26:54] : =================================================================== CHECK 1 ===================================================================
[2023-01-04 10:26:54] :
[2023-01-04 10:26:54] : - Contacting DC in AD domain ...[DC3.<domain>]...(SOURCE RWDC)
[2023-01-04 10:26:54] : * DC is Reachable...
[2023-01-04 10:26:54] : * The new password for Object [CN=krbtgt_19109_TEST,CN=Users,DC=<domain>,DC=local] exists in the AD database
[2023-01-04 10:26:54] :
[2023-01-04 10:26:54] : - Contacting DC in AD domain ...[RODC1.<domain>]...
[2023-01-04 10:26:54] : * DC is Reachable...
[2023-01-04 10:26:56] : * The new password for Object [CN=krbtgt_19109_TEST,CN=Users,DC=<domain>,DC=local] now does exist in the AD database
[2023-01-04 10:26:56] :
[2023-01-04 10:26:56] :
[2023-01-04 10:26:56] : --> Start Time......: 2023-01-04 10:26:54
[2023-01-04 10:26:56] : --> End Time........: 2023-01-04 10:26:56
[2023-01-04 10:26:56] : --> Duration........: 2.34 Seconds
[2023-01-04 10:26:56] :
[2023-01-04 10:26:56] :
[2023-01-04 10:26:56] : List Of DCs In AD Domain '<domain>' And Their Timing...
[2023-01-04 10:26:56] :
[2023-01-04 10:26:56] :
Host Name PDC Site Name DS Type IP Address Reachable Source RWDC FQDN Time
--------- --- --------- ------- ---------- --------- ---------------- ----
DC3.<domain> False SiteHQ Read/Write 10.10.14.153 True N.A. 0
RODC1.<domain> False Site1 Read-Only 172.17.18.10 True DC3.<domain> 2.34