- Ethical-hacking
- Introduction
- Steps of Pen-Testing
- Enumeration
- Privilege Escalation
- Testing
- Tools and resouces
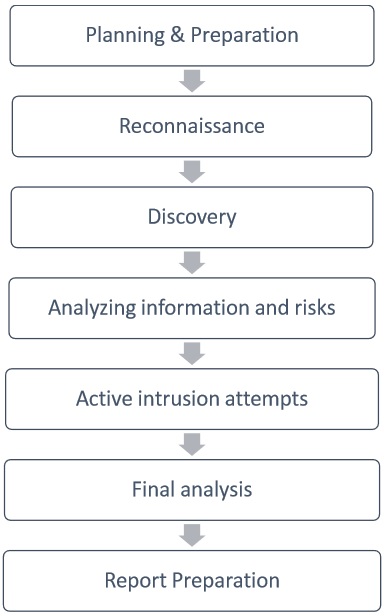
Certainly, I can provide a detailed explanation of each step in the ethical hacking process. Please keep in mind that this information is for educational purposes and should only be used in a legal and ethical manner.
1. Planning and Reconnaissance:
-
Define the Scope: Clearly define the scope of the engagement. Identify the systems, networks, or applications that you are authorized to test. Make sure you have written permission.
-
Gather Information: Use various resources, including WHOIS databases, DNS records, and public information, to gather information about the target's domain, IP ranges, and more.
-
Footprinting: This involves collecting data on the target's infrastructure, such as subdomains, IP addresses, network architecture, and technology in use.
2. Scanning:
-
Port Scanning: Use tools like Nmap to perform port scanning, identifying open ports and services on the target systems. Understand potential attack vectors.
-
Vulnerability Scanning: Utilize tools like Nessus, OpenVAS, or Qualys to scan for known vulnerabilities in the target's systems, applications, and services.
3. Gaining Access:
-
Exploitation: Based on the vulnerabilities discovered, use tools like Metasploit to exploit them. Metasploit provides pre-built exploits, payloads, and post-exploitation modules.
-
Password Cracking: Attempt to crack passwords using tools like John the Ripper, Hashcat, or Hydra. This can be used to gain unauthorized access.
4. Maintaining Access:
- Backdoors and Trojans: Create persistent access points using backdoors or Trojans. This might involve installing a hidden remote access tool that allows continued control.
5. Analysis:
-
Review Results: Analyze the results of your testing, including vulnerabilities identified, their severity, and potential impact on the target systems.
-
Risk Assessment: Evaluate the risks associated with the vulnerabilities. Consider the likelihood of exploitation and the potential business impact.
6. Documentation:
-
Report Writing: Prepare a comprehensive report detailing your findings, including vulnerabilities, their impact, and recommended remediation steps.
-
Evidence Preservation: Document all steps taken during testing, including commands used, tools employed, and screenshots. This documentation can serve as evidence of your ethical hacking activities.
7. Remediation:
-
Notify the Client: Communicate your findings and recommendations to the client. Provide clear explanations of the vulnerabilities and their potential impact.
-
Patching and Mitigation: Assist the client in addressing vulnerabilities by applying patches, changing configurations, and implementing security measures to mitigate the risks.
8. Validation and Verification:
-
Re-Test: After the client has taken action to address the vulnerabilities, perform a re-test to confirm that the issues have been resolved and the systems are more secure.
-
Verification: Ensure that the security measures put in place are effective and that the systems are now adequately protected against potential threats.
9. Education and Improvement:
-
Training: Provide security training to the client's team to enhance their understanding of security practices, vulnerability management, and incident response.
-
Continuous Improvement: Encourage the client to establish an ongoing security monitoring program, regularly update software, and conduct periodic vulnerability assessments to maintain a secure environment.
The goal of this repository is to help out beginners-medium hackers. Practicing is the only way to improve in this domain, and there are plenty of websites where you can learn, and hack at the same time. But before that, let's talk a bit about what you will find in the repository.
To become a great pentester you have to be patient. Learning and practicing are definetly your way into this domain. But it will take some time. Here's a simple list of things you should and shouldn't do in order to imporve :
- You have to master at least one programming language. And if you still haven't learn a single programming language, I would advise you to start with C.
- Don't just use tools without knowing how they work. Here's a list of tools you will need.
- You're not ready for real targets, just focus on practicing and learning and you will get there. Hopefully in a lawful way.
- Learning doesn't only rely on videos on youtube, reading could be a great way as well. From books to manuals and articles.
- Don't be a script kiddie, not having any idea on what you're doing means you're a script kiddie.
- Assembly language is far important than you think, specially if you're into Reverse engineeering or PWN. It would be easier to learn it if you master C language before.
- You have to know how computers and operating system works. Do you know what a kernel is ? If not you should do some googling.
- Twitter, as dumb as this idea looks, but I'd really recommend you to have a twitter account, and follow communities related to cyber security. Staying up to date with the world is not such a bad idea after all.
- Last but not least, don't learn hacking for wrong reasons. Don't waste your time if your goal is to hack your girlfriends Facebook account. Set a goal, no matter how big it looks like, and chase it. Dreams without goals are the ultimate fuel of disappointment.
Here's a list of one the best youtubers I personally follow.
| Name | Description | Link |
|---|---|---|
| Liveoverflow | One of the best channels on youtube to learn reverse engineering and PWN. | link |
| IPPSEC | Does retired machines from HackTheBox, great way to learn what to do before every machine. | Link |
| John Hammond | Does different kind of CTFs, you can learn how to use lot of tools, and techniques. | Link |
| David Bombal | Great channel to imporve professionally in hacking if you are looking for jobs. | Link |
| NetworkChuck | If you are looking where to learn very basic stuff with a fun way, this guy is yours. | Link |
| CryptoCat | Although this channel is newly, it has some really great content you definetly should check | link |
| HackerSploit | This one explains tools, and does HackTheBox retired machines. And also does real life scenarios hacking | Link |
| Here's the list with the content reformatted as requested: | ||
| Black Hat | ... | link |
| Injector Pca | ... | link |
| Hisham Mir | ... | link |
| Devil Killer | ... | link |
| Suleman Malik | ... | link |
| Dem0n | ... | link |
| Frans Rosén | ... | link |
| HackerOne | ... | link |
| ak1t4 machine | ... | link |
| Shawar Khan | ... | link |
| vulnerability0lab | ... | link |
| Bugcrowd | ... | link |
| Vijay Kumar | ... | link |
| Web Development Tutorials | ... | link |
| Jan Wikholm | ... | link |
| Bhargav Tandel | ... | link |
| ErrOr SquaD | ... | link |
| SecurityIdiots | ... | link |
| Penetration Testing in Linux | ... | link |
| Hussnain Fareed | ... | link |
| Null Byte | ... | link |
| ZAID | ... | link |
| vabs tutorial | ... | link |
| the cyber mentor | ... | link |
| PwnFunction | ... | link |
| GetCyber | ... | link |
Here you will find multiple resources to learn and practice hacking.
Here's where you can learn and practice at the same time.
| Name | Description | Link |
|---|---|---|
| HackTheBox | Perhaps the greatest platform with the hardest possible challenge. specialise in Boxes | HackTheBox |
| TryHackMe | This one is similar to HackTheBox, difference is that is has easier challenges than HTB | TryHackMe |
| PwnTillDawn | Although the name would give you PWN vibes, it has a big number of boxes ready to be PWNed | PwnTillDawn |
| CyberTalents | A good platform for beginners to start their journey into hacking. It has only CTFs though | CyberTalents |
| Pwnable | Fun platform to learn PWN from the very basics. You will need to learn C language before | Pwnable |
| HackThisSite | Free platform for hackers to test and expand their knowledge with CTFs, challenges and many more | HackThisSite |
| Hacker101 | Free class for web security. Whether you're a programmer with an interest in bug bounties or a seasoned security professional | Hacker101 |
| PicoCTF | Free computer security education program, with original created challenges to practice your skills in different domains. | PicoCTF |
| PortSwigger | PortSwigger is a widely-used platform for web application security testing and ethical hacking. | PortSwigger |
| CTF Hacker101 | The Hacker101 CTF is a game designed to let you learn to hack in a safe, rewarding environment. Hacker101 is a free educational site for hackers. | CTF Hacker101 |
| CTF365 | An account based ctf site, awarded by Kaspersky, MIT, T-Mobile. | CTF365 |
| Backdoor | Pen testing labs that have a space for beginners, a practice arena and various competitions, account required. | Backdoor |
| Hack.me | Lets you build/host/attack vulnerable web apps. | Hack.me |
| CTFLearn | An account-based ctf site, where users can go in and solve a range of challenges. | CTFLearn |
| OWASP Vulnerable Web Applications Directory Project (Online) | List of online available vulnerable applications for learning purposes. | OWASP Vulnerable Web Applications Directory Project (Online) |
| Pentestit labs | Hands-on Pentesting Labs (OSCP style) | Pentestit labs |
| Root-me.org | Hundreds of challenges are available to train yourself in different and not simulated environments | Root-me.org |
| Vulnhub.com | Vulnerable By Design VMs for practical 'hands-on' experience in digital security | Vulnhub.com |
| Windows / Linux Local Privilege Escalation Workshop | Practice your Linux and Windows privilege escalation. | Windows / Linux Local Privilege Escalation Workshop |
| Hacking Articles | CTF Brief Write up collection with a lot of screenshots good for beginners. | Hacking Articles |
| Rafay Hacking Articles, a great blog | Write up collections by Rafay Baloch. | Rafay Hacking Articles, a great blog |
| PentesterLab | 20$ signature, complete content basic to write exploits, web, android. | PentesterLab |
| CyberSec WTF | Emulated web pentesting challenges from bounty write-ups | CyberSec WTF |
Go ahead a knock yourself out.
There are certain things you need to learn before even diving into hacking. Here's a list you should definetly check out.
Many might think that programming is not really necessary in hacking, they're not just wrong they're stupid. But you need to know that not all programming languages serve the same purpose. There are different types, you should learn at least one language in each category. Let's go ahead and check them out.
These are the languages that will on a daily basis in your hacking journey.
- C / Assembly : Low level language, for binary exploitation.
- Bash : Linux scripting language.
- Powershell : Windows scripting language.
- Python : Easy to learn language, that can help you automate lot of work you do frequently.
- PHP : You cannot do bug bounty without knowing PHP.
- Javascript : Learning Javascript is as important as learning PHP, specially if you are into Bug Bounty.
- C++
- Ruby
- Lua
- Java
- Perl
In this section, We'll give you a certain steps you should always follow when you're pentesting.
Now since we're finished with the introduction, let's go ahead and hack a box for the sake of an example. The Box I chose, is Boot2Root, a project in 42 Cursus.
The first step you should think of, is trying to identify what exactly you're attacking(hopefully in a lawful way). You need to gather maximum of informations from this target. A great way to do so, is to use a tool called NMAP. It's used to to scan ip addresses, it can also be used to identify ip addresses connected to your network. Since we do not know the ip address of our box, we have to scan our network in order to identify its ip address.
Depending on what's your network class, you can use the following command in order to scan a certain subnet.
$> nmap 10.12.100.x/24You will get an output similar to this :
And as you can see we have the ip address of the machine. But you'll ask what else we can do with nmap. Great question, can't answer it all. You have to discover more yourself. But let me show you some couple of commands you can use in order to do stuff.In order to use the following commands, you have to specify -A tag on your scan. It for aggressive scanning.
$> nmap -A 10.12.11.100Using nmap, you can detect what Operatin System the target uses. Note that this is not always accurate, and also you will need root privelege. Here's an example :
$> sudo nmap -o 10.12.11.100You can also detect what services are running on that target, the version of those services as well. Note that -sV is for the version scanning.
$> nmap -sV 10.12.11.100How about running a scan on all the ports from in a total of 65,535 ports.
$> nmap -p- 10.12.11.100You want only one port ?
$> nmap -p 80 10.22.11.100How about multiple ports ?
$> nmap -p 80,443 10.22.11.100A range of ports ?
$> nmap -p 80-8080 10.22.11.100There is also timing templates, if you want your scan to take more or less time.
$> nmap -T[ID] 10.22.11.100Sometimes you will counter targets that blocks your pings. Use the -Pn tag to skip the host discovery. This treats your target as an online target.
$> nmap -Pn 10.22.11.100If you want to save the results of your scan you can do it like this :
$> nmap 10.22.11.100 -oA output.nameLet's go ahead and gather all the tags, under one powerful command, you have to know that a command like this would take ~20-30 minutes :
$> sudo nmap -A -O -Pn -p- -T4 -sV 10.22.11.100There are a lot more commands than this, you should visit the nmap man page or their Docs to learn even more about this tool.
There are lot of other tools that you can use in order to dir bust, and each tools gives you different options.
Let's say you scanned a target and you found a web application, this web application can contains a multiple subdomains that you should check.
You might ask what a subdomain is. It's simply a good way to seperate the content of you website. It's piece of additional information added to the beginning of a website’s domain name. It allows websites to separate and organize content for a specific function — such as a blog or an online store — from the rest of your website.
Like sub-directories, you can also search for sub-domains , using a wordlist and a tool. In this case we'll be using as an example gobuster
Using the following command :
$> gobuster dns -d google.com -w /path/to/wordlist.txt
-d : To specify the domain name
-w : To specify a wordlistThus you will get something like this(don't take this example seriously, it's not true... or maybe ?).
www.google.com
blog.google.com
store.google.com
etc...
This can help you find more information about a certain website that you didn't know. Maybe even find login pannels or so.
After generating a list of subdomain and hosts, it's time to check those who work. Doing it manualy will take a long time if a long list was generated, so here's a tools httpx that make that task easy for us. Using the following command :
$> cat hosts.txt | httpxhttpx have more other intersting functionality, check the repo for more info.
You find a web app and its subdomains too, so what can you do with it. For instance you can try and find directories or files. There are lot of tools you can use to do that. But for now let's use dirb.
You'll need wordlist, in order to test on multiple directories or files. Check wordlists for more infos.
This is an example on how to use dirb command.
$> dirb http://ip_add/ /path/to/wordlistA good thing to do is to pay attention to the request you make on a website. Some websites can show you different outputs depending on what domain name you requested. Specially when you're playing challenges on websites like HackTheBox or TryHackMe, always change your host file to whatever you find while scanning or while enumerating in general.
$> nano /etc/hosts
10.1.1.1 1337.htb #exampleLogs are really important when it comes to tracing one's moves. You can even find credentials on them. We will talk more about it in the Privilege Escalation part
Using HackTricks, we can use multiple commands to monitor a system and thus finding an exploit we can use to privesc the system.
uname -a
cat /etc/os-release
cat /proc/version
uname -r
sudo -v (might not work sometimes if you don't have the password of the user)
ps aux
ps -ef
top -n 1
crontab -l
ls -al /etc/cron* /etc/at*
cat /etc/cron* /etc/at* /etc/anacrontab /var/spool/cron/crontabs/root 2>/dev/null | grep -v "^#"
Since we were inspired by this readme to do one where we can always contribute to it, and it won't be just the usual stuff you read online. Here you will find a list of tools by category. You can also visit the official website of Kali Linux for more information.
Information Gathering tools allows you to collect host metadata about services and users. Check informations about a domain, IP address, phone number or an email address.
| Tool | Language | Support | Description |
|---|---|---|---|
| theHarvester | Python | Linux/Windows/macOS |
E-mails, subdomains and names Harvester. |
| CTFR | Python | Linux/Windows/macOS |
Abusing Certificate Transparency logs for getting HTTPS websites subdomains. |
| Sn1per | bash | Linux/macOS |
Automated Pentest Recon Scanner. |
| RED Hawk | PHP | Linux/Windows/macOS |
All in one tool for Information Gathering, Vulnerability Scanning and Crawling. A must have tool for all penetration testers. |
| Infoga | Python | Linux/Windows/macOS |
Email Information Gathering. |
| KnockMail | Python | Linux/Windows/macOS |
Check if email address exists. |
| a2sv | Python | Linux/Windows/macOS |
Auto Scanning to SSL Vulnerability. |
| Wfuzz | Python | Linux/Windows/macOS |
Web application fuzzer. |
| Nmap | C/C++ | Linux/Windows/macOS |
A very common tool. Network host, vuln and port detector. |
| PhoneInfoga | Go | Linux/macOS |
An OSINT framework for phone numbers. |
Crack passwords and create wordlists.
| Tool | Language | Support | Description |
|---|---|---|---|
| John the Ripper | C | Linux/Windows/macOS |
John the Ripper is a fast password cracker. |
| hashcat | C | Linux/Windows/macOS |
World's fastest and most advanced password recovery utility. |
| Hydra | C | Linux/Windows/macOS |
Parallelized login cracker which supports numerous protocols to attack. |
| ophcrack | C++ | Linux/Windows/macOS |
Windows password cracker based on rainbow tables. |
| Ncrack | C | Linux/Windows/macOS |
High-speed network authentication cracking tool. |
| WGen | Python | Linux/Windows/macOS |
Create awesome wordlists with Python. |
| SSH Auditor | Go | Linux/macOS |
The best way to scan for weak ssh passwords on your network. |
| Tool | Description |
|---|---|
| Probable Wordlist | Wordlists sorted by probability originally created for password generation and testing. |
Used for intrusion detection and wifi attacks.
| Tool | Language | Support | Description |
|---|---|---|---|
| Aircrack | C | Linux/Windows/macOS |
WiFi security auditing tools suite. |
| bettercap | Go | Linux/Windows/macOS/Android |
bettercap is the Swiss army knife for network attacks and monitoring. |
| WiFi Pumpkin | Python | Linux/Windows/macOS/Android |
Framework for Rogue Wi-Fi Access Point Attack. |
| Airgeddon | Shell | Linux/Windows/macOS |
This is a multi-use bash script for Linux systems to audit wireless networks. |
| Airbash | C | Linux/Windows/macOS |
A POSIX-compliant, fully automated WPA PSK handshake capture script aimed at penetration testing. |
Acesss systems and data with service-oriented exploits.
| Tool | Language | Support | Description |
|---|---|---|---|
| SQLmap | Python | Linux/Windows/macOS |
Automatic SQL injection and database takeover tool. |
| XSStrike | Python | Linux/Windows/macOS |
Advanced XSS detection and exploitation suite. |
| Commix | Python | Linux/Windows/macOS |
Automated All-in-One OS command injection and exploitation tool. |
| Nuclei | Go | Linux/Windows/macOS |
Fast and customisable vulnerability scanner based on simple YAML based DSL. |
Listen to network traffic or fake a network entity.
| Tool | Language | Support | Description |
|---|---|---|---|
| Wireshark | C/C++ | Linux/Windows/macOS |
Wireshark is a network protocol analyzer. |
| WiFi Pumpkin | Python | Linux/Windows/macOS/Android |
Framework for Rogue Wi-Fi Access Point Attack. |
| Zarp | Python | Linux/Windows/macOS |
A free network attack framework. |
Exploit popular CMSs that are hosted online.
| Tool | Language | Support | Description |
|---|---|---|---|
| WPScan | Ruby | Linux/Windows/macOS |
WPScan is a black box WordPress vulnerability scanner. |
| Droopescan | Python | Linux/Windows/macOS |
A plugin-based scanner to identify issues with several CMSs, mainly Drupal & Silverstripe. |
| Joomscan | Perl | Linux/Windows/macOS |
Joomla Vulnerability Scanner. |
| Drupwn | Python | Linux/Windows/macOS |
Drupal Security Scanner to perform enumerations on Drupal-based web applications. |
| CMSeek | Python | Linux/Windows/macOS |
CMS Detection and Exploitation suite - Scan WordPress, Joomla, Drupal and 130 other CMSs. |
Exploits for after you have already gained access.
| Tool | Language | Support | Description |
|---|---|---|---|
| TheFatRat | C | Linux/Windows/macOS |
Easy tool to generate backdoor and easy tool to post exploitation attack like browser attack, dll. |
Frameworks are packs of pen testing tools with custom shell navigation and documentation.
| Tool | Language | Support | Description |
|---|---|---|---|
| Operative Framework | Python | Linux/Windows/macOS |
Framework based on fingerprint action, this tool is used to get information on a website or a enterprise target with multiple modules. |
| Metasploit | Ruby | Linux/Windows/macOS |
A penetration testing framework for ethical hackers. |
| cSploit | Java | Android |
The most complete and advanced IT security professional toolkit on Android. |
| radare2 | C | Linux/Windows/macOS/Android |
Unix-like reverse engineering framework and commandline tools. |
| Wifiphisher | Python | Linux |
The Rogue Access Point Framework. |
| Beef | Javascript | Linux/Windows/macOS |
The Browser Exploitation Framework. It is a penetration testing tool that focuses on the web browser. |
| Mobile Security Framework (MobSF) | Python | Linux/Windows/macOS |
Mobile Security Framework (MobSF) is an automated, all-in-one mobile application (Android/iOS/Windows) pen-testing, malware analysis and security assessment framework capable of performing static and dynamic analysis. |
| Burp Suite | Java | Linux/Windows/macOS |
Burp Suite is a leading range of cybersecurity tools, brought to you by PortSwigger. This tool is not free and open source |
Ensure you have permission before conducting any testing!
-
Reconnaissance
a. Passive
-
Google Dorking:
site:example.com, inurl, intext, etc. -
WHOIS Lookup:
whois example.com -
DNS Recon:
dnsrecon -d example.com
b. Active
-
Nmap:
nmap -sn <IP_range>(ping sweep) -
Nmap:
nmap -p- <target_IP>(port scanning)
-
-
Enumeration
a. DNS Enumeration
- Dig:
dig @<DNS_server> example.com AXFR - Nmap:
nmap --script dns-brute <target_IP>
b. SMB Enumeration
- Nmap:
nmap --script smb-enum-shares <target_IP> - Smbclient:
smbclient \\\\<target_IP>\\<share_name> -U <username>
c. SNMP Enumeration
- Snmpwalk:
snmpwalk -c public -v1 <target_IP> - Onesixtyone:
onesixtyone <target_IP>
d. Web Application Enumeration
- Nikto:
nikto -h <target_URL> - Dirb:
dirb <target_URL>
- Dig:
-
Vulnerability Assessment
a. Nmap NSE Scripts
- Nmap:
nmap --script vuln <target_IP>
b. OpenVAS
- Setup and run OpenVAS on target systems
c. Metasploit Framework
-
Search for modules:
search <vulnerability> -
Use a module:
use <module_name>
- Nmap:
-
Exploitation
a. Metasploit Framework
- Set options:
set <option> <value> - Run exploit:
exploit or run
b. Manual Exploitation
- Research and use known exploits for identified vulnerabilities
c. Web Application Exploitation
-
SQL Injection:
sqlmap -u <target_URL> -
XSS: Test payloads, use automated tools like
XSStrike
- Set options:
-
Post-Exploitation
a. Privilege Escalation
- Linux:
linPEAS, LinEnum - Windows:
winPEAS, PowerUp, Sherlock
b. Lateral Movement
- PsExec:
psexec.py <username>:<password>@<target_IP> - Mimikatz:
sekurlsa::logonpasswords
c. Data Exfiltration
- Identify and collect sensitive information
- Linux:
-
Clean Up
Remove artifacts, backdoors, and logs
-
Reporting
Document findings, recommendations, and mitigations
Tools and Resources:
Certainly, here's a more detailed list
- WHOIS Lookup: Obtain domain registration information and contact details.
- Shodan: Search engine for internet-connected devices and services.
- theHarvester: Gather email addresses, subdomains, and information from public sources.
- Recon-ng: A reconnaissance framework that collects data from various sources.
- Maltego: Visualize relationships between gathered information using graphs.
- SpiderFoot: OSINT automation tool to collect data from different sources.
- FOCA: Extract metadata and information from documents for analysis.
- Sublist3r: Subdomain enumeration tool using various search engines.
- Censys: Discover hosts and networks on the internet and gather information.
- Amass: In-depth subdomain enumeration and information gathering.
- Nmap: Versatile network discovery and port scanning tool.
- Masscan: High-speed port scanner designed for large-scale scans.
- Zmap: Fast network scanner for exploring the entire IPv4 address space.
- Unicornscan: Lightweight network scanner with asynchronous scanning capabilities.
- RustScan: Fast and efficient port scanner written in Rust.
- Nessus: Commercial vulnerability scanner that includes port scanning capabilities.
- Angry IP Scanner: Cross-platform IP address and port scanner.
- Amap: Application layer scanner for identifying open ports and services.
- Hping3: Network tool for crafting packets and sending them over the network.
- SuperScan: Windows-based port scanner with additional features.
- Nessus: Widely used vulnerability scanner for identifying known vulnerabilities.
- OpenVAS: Open-source vulnerability scanner and manager.
- Qualys: Cloud-based security platform offering vulnerability management.
- Nexpose: Vulnerability management tool by Rapid7, now part of InsightVM.
- Retina: Network vulnerability assessment tool by BeyondTrust.
- Metasploit Framework: Popular exploitation framework for penetration testers.
- Canvas: Commercial exploitation framework for advanced security professionals.
- Core Impact: Commercial penetration testing framework with exploitation capabilities.
- BeEF: Browser exploitation framework for targeting web browsers.
- SET (Social-Engineer Toolkit): Toolkit for social engineering attacks and exploitation.
- Armitage: Metasploit GUI that simplifies exploitation and post-exploitation.
- Empire: Post-exploitation framework with agent-based control.
- RouterSploit: Framework for exploiting embedded devices.
- CrackMapExec: Post-exploitation tool for network pivoting and lateral movement.
- RouterSploit: Framework for exploiting embedded devices.
- John the Ripper: Password cracking tool for various encryption algorithms.
- Hashcat: Powerful password cracking tool with GPU acceleration.
- Hydra: Fast and flexible online password cracking tool.
- Medusa: Speedy parallelized network login brute-forcer.
- Cain and Abel: Windows-based password recovery tool.
- RainbowCrack: Crack password hashes using precomputed tables.
- Patator: Multi-purpose brute-forcing tool.
- Hashcat: Powerful password cracking tool with GPU acceleration.
- Hydra: Fast and flexible online password cracking tool.
- Medusa: Speedy parallelized network login brute-forcer.
- Netcat (nc): Networking utility for creating reverse shells and backdoors.
- Meterpreter: Part of the Metasploit Framework, provides advanced post-exploitation capabilities.
- Empire: Powerful post-exploitation framework for Windows environments.
- Cobalt Strike: Adversary simulation and red teaming platform.
- Veil: Framework for generating undetectable payloads and backdoors.
- Pupy: Cross-platform remote administration and post-exploitation tool.
- RATs: Remote Administration Tools like DarkComet, NanoCore, and others.
- Beacon: Part of Cobalt Strike, offers advanced post-exploitation functionality.
- Empire: Powerful post-exploitation framework for Windows environments.
- Cobalt Strike: Adversary simulation and red teaming platform.
- LaTeX: Document preparation system for high-quality documents.
- Microsoft Word: Standard word processor for creating comprehensive reports.
- Markdown: Lightweight markup language for creating formatted text.
- JIRA: Project management and collaboration tool for documenting tasks and progress.
- Confluence: Collaboration tool for creating, sharing, and collaborating on documentation.
- MISP: Threat intelligence platform for documenting and sharing threat data.
- Dradis: Reporting and collaboration platform that integrates with other security tools.
- Evernote: Note-taking and organization tool for documentation.
- Git/GitHub: Version control system and platform for collaborating on documentation.
- Wireshark: Network protocol analyzer that helps with documentation and analysis.
Certainly, here's the provided content formatted as requested:
- Devbreak on Twitter
- The Life of a Security Researcher
- Find an awesome hacking spots in your country
- Awesome-Hacking Lists
- Crack Station
- Exploit Database
- Hackavision
- Hackmethod
- Packet Storm Security
- SecLists
- SecTools
- Smash the Stack
- Don't use VPN services
- How to Avoid Becoming a Script Kiddie
- 2017 Top 10 Application Security Risks
- Starting in cybersecurity ?
I would highly advise you guys to go and checkout sundowndev
| Name | Description |
|---|---|
| Malware traffic analysis | List of traffic analysis exercises |
| Malware Analysis - CSCI 4976 | Another class from the folks at RPISEC, quality content |
| Bad Binaries | Walkthrough documents of malware traffic analysis exercises and some occasional malware analysis. |
| Name | Description |
|---|---|
| Kali | The infamous pentesting distro from the folks at Offensive Security |
| Parrot | Debian includes full portable lab for security, DFIR, and development |
| Android Tamer | Android Tamer is a Virtual / Live Platform for Android Security professionals. |
| BlackArch | Arch Linux based pentesting distro, compatible with Arch installs |
| LionSec Linux | Pentesting OS based on Ubuntu |
For those who want to do CEH, the following links are for you. 2. CBT Nuggets CEH Training 3. CEH Books 4. Guide to Binary Exploitation
- InfoCon - Hacking Conference Archive
- Curated list of Security Talks and Videos
- Blackhat
- Defcon
- Security Tube
- Kevin Mitnick: Live Hack at CeBIT
- Ghost in the Cloud, Kevin Mitnick
- Kevin Mitnick | Talks at Google
- Complete Free Hacking Course: Go from Beginner to Expert Hacker Today
Here's the provided content formatted as requested:
| Name | Description |
|---|---|
| 0x00sec | Hacker, malware, computer engineering, reverse engineering |
| Antichat | Russian-based forum |
| CODEBY.NET | Hacker, WAPT, malware, computer engineering, reverse engineering, forensics - Russian-based forum |
| EAST Exploit database | Exploit DB for commercial exploits written for EAST Pentest Framework |
| Greysec | Hacking and security forum |
| Hackforums | Posting website for hacks, exploits, and various discussions |
These tools cover various aspects of ethical hacking and penetration testing, but remember that ethical hacking requires responsible and legal use. Always ensure you have proper authorization before using any tools on a target environment.
Remember that each step requires careful consideration of legal and ethical boundaries, and proper authorization is essential before proceeding. The detailed process outlined here is a guideline and can be adapted based on the specific engagement's requirements and the tools available. Always prioritize responsible and ethical behavior when conducting any form of ethical hacking.