Detailed information about how to use, configure and extend this module can be found on our Wiki:
The Azure landing zones Terraform module is designed to accelerate deployment of the Azure landing zones conceptual architecture using Terraform.
Using a very simple initial configuration, the module will deploy the recommended core Management Group hierarchy, including the recommended governance baseline using Azure Policy. The default configuration can be easily extended to meet differing requirements, and includes the ability to deploy platform resources.
This is currently split logically into the following capabilities:
These resources can be deployed to multiple Subscriptions by setting the Provider Configuration on the module block.
The following sections outline the different resource types deployed and managed by this module, depending on the configuration options specified.
The core capability of this module deploys the foundations of the Azure landing zones conceptual architecture, with a focus on resource hierarchy and governance:
The following resource types are deployed and managed by this module when using the core capabilities:
| Azure Resource | Terraform Resource | |
|---|---|---|
| Management Groups | Microsoft.Management/managementGroups |
azurerm_management_group |
| Management Group Subscriptions | Microsoft.Management/managementGroups/subscriptions |
azurerm_management_group |
| Policy Assignments | Microsoft.Authorization/policyAssignments |
azurerm_management_group_policy_assignment |
| Policy Definitions | Microsoft.Authorization/policyDefinitions |
azurerm_policy_definition |
| Policy Set Definitions | Microsoft.Authorization/policySetDefinitions |
azurerm_policy_set_definition |
| Role Assignments | Microsoft.Authorization/roleAssignments |
azurerm_role_assignment |
| Role Definitions | Microsoft.Authorization/roleDefinitions |
azurerm_role_definition |
The exact number of resources created depends on the module configuration, but you can expect upwards of 200 resources to be created by this module for a default installation based on the example below.
NOTE: None of these resources are deployed at the Subscription scope, however Terraform still requires a Subscription to establish an authenticated session with Azure.
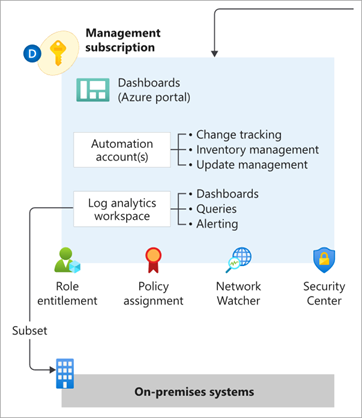
The module includes functionality to enable deployment of Management and monitoring resources into the Subscription context set by the azurerm.management provider alias.
This brings the benefit of being able to manage the full lifecycle of these resources using Terraform, with native integration into the corresponding Policy Assignments to ensure full policy compliance.
The following resource types are deployed and managed by this module when the Management capabilities are enabled:
| Azure Resource | Terraform Resource | |
|---|---|---|
| Resource Groups | Microsoft.Resources/resourceGroups |
azurerm_resource_group |
| Log Analytics Workspace | Microsoft.OperationalInsights/workspaces |
azurerm_log_analytics_workspace |
| Log Analytics Solutions | Microsoft.OperationsManagement/solutions |
azurerm_log_analytics_solution |
| Automation Account | Microsoft.Automation/automationAccounts |
azurerm_automation_account |
| Log Analytics Linked Service | Microsoft.OperationalInsights/workspaces /linkedServices |
azurerm_log_analytics_linked_service |
Please refer to the Deploy Management Resources page on our Wiki for more information about how to use this capability.
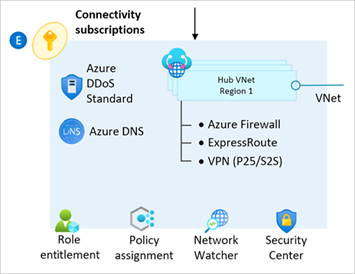
The module enables deployment of Network topology and connectivity resources into the Subscription context set by the azurerm.connectivity provider alias.
The module supports creating multiple hubs (one per specified location) in both a Hub and Spoke or Virtual WAN configuration.
There are also additional supporting resources deployed for DDoS Protection and DNS zones.
You can also create a combination of both networks.
Each hub can be individually configured as needed.
NOTE: The module currently only configures the networking hub, and dependent resources for the
ConnectivitySubscription. To ensure we achieve the right balance of managing resources via Terraform vs. Azure Policy, we are still working on how best to handle the creation of spoke Virtual Networks and Virtual Network Peering (forHub and Spokenetworks). Improving this story is our next priority on the product roadmap.
The following resource types are deployed and managed by this module when the Connectivity capabilities are enabled:
Further guidance on how to deploy and configure Hub and Spoke networks can be found on the Deploy Connectivity Resources Wiki page.
Further guidance on how to deploy and configure Virtual WAN networks will be added to the Wiki in the future.
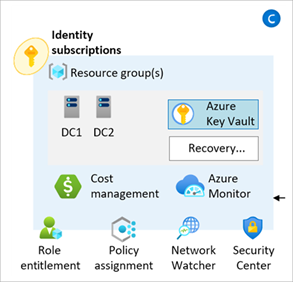
The module enables deployment and configuration of Azure Policy to control governance over the Identity and access management Subscription.
No additional resources are currently deployed by this capability, however policy settings relating to the Identity Management Group can be easily updated via the configure_identity_resources input variable.
Please refer to the Deploy Identity Resources page on our Wiki for more information about how to use this capability.
This module has been tested using Terraform 0.15.1 and AzureRM Provider 3.0.2 as a baseline, and various versions to up the latest at time of release.
In some cases, individual versions of the AzureRM provider may cause errors.
If this happens, we advise upgrading to the latest version and checking our troubleshooting guide before raising an issue.
We recommend starting with the following configuration in your root module to learn what resources are created by the module and how it works.
This will deploy the core components only.
NOTE: For production use we highly recommend using the Terraform Registry and pinning to the latest stable version, as per the example below. Pinning to the
mainbranch in GitHub will give you the latest updates quicker, but increases the likelihood of unplanned changes to your environment and unforeseen issues.
# Configure Terraform to set the required AzureRM provider
# version and features{} block.
terraform {
required_providers {
azurerm = {
source = "hashicorp/azurerm"
version = ">= 3.0.2"
}
}
}
provider "azurerm" {
features {}
}
# Get the current client configuration from the AzureRM provider.
# This is used to populate the root_parent_id variable with the
# current Tenant ID used as the ID for the "Tenant Root Group"
# Management Group.
data "azurerm_client_config" "core" {}
# Use variables to customize the deployment
variable "root_id" {
type = string
default = "es"
}
variable "root_name" {
type = string
default = "Enterprise-Scale"
}
# Declare the Azure landing zones Terraform module
# and provide a base configuration.
module "enterprise_scale" {
source = "Azure/caf-enterprise-scale/azurerm"
version = "2.1.0"
providers = {
azurerm = azurerm
azurerm.connectivity = azurerm
azurerm.management = azurerm
}
root_parent_id = data.azurerm_client_config.core.tenant_id
root_id = var.root_id
root_name = var.root_name
}For additional guidance on how to customize your deployment using the advanced configuration options for this module, please refer to our User Guide and the additional examples in our documentation.
Please refer to our Module Permissions guide on the Wiki.
For the latest examples, please refer to our Examples guide on the Wiki.
Please see the releases page for the latest module updates.
For upgrade guides from previous versions, please refer to the following links:
- Upgrade from v1.1.4 to v2.0.0
- Upgrade from v0.4.0 to v1.0.0
- Upgrade from v0.3.3 to v0.4.0
- Upgrade from v0.1.2 to v0.2.0
- Upgrade from v0.0.8 to v0.1.0
The following statement is applicable from release v2.0.0 onwards
When you deploy one or more modules using the Azure landing zones Terraform module, Microsoft can identify the installation of said module/s with the deployed Azure resources. Microsoft can correlate these resources used to support the software. Microsoft collects this information to provide the best experiences with their products and to operate their business. The telemetry is collected through customer usage attribution. The data is collected and governed by Microsoft's privacy policies.
If you don't wish to send usage data to Microsoft, details on how to turn it off can be found here.