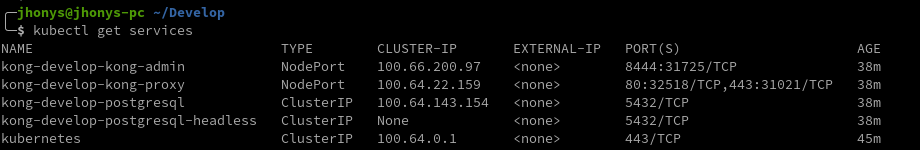
I am trying to deploy keycloak using Mysql, the charts works just fine when replica is set to 1, but it doesn't work when it's greater than 1 (eg: 2 or 3). Actually I can see the main athentication page, but once I clic on "Log In" I get ERR_TOO_MANY_REDIRECTS error.
09:41:53,225 WARN [org.keycloak.events] (default task-1) type=LOGIN_ERROR, realmId=master, clientId=null, userId=null, ipAddress=10.38.0.0, error=expired_code, restart_after_timeout=true
09:41:53,351 WARN [org.keycloak.events] (default task-1) type=LOGIN_ERROR, realmId=master, clientId=null, userId=null, ipAddress=10.38.0.0, error=expired_code, restart_after_timeout=true
09:41:53,480 WARN [org.keycloak.events] (default task-1) type=LOGIN_ERROR, realmId=master, clientId=null, userId=null, ipAddress=10.38.0.0, error=expired_code, restart_after_timeout=true
09:42:45,412 WARN [org.keycloak.events] (default task-4) type=LOGIN_ERROR, realmId=master, clientId=null, userId=null, ipAddress=10.32.0.1, error=expired_code, restart_after_timeout=true
09:42:45,672 WARN [org.keycloak.events] (default task-4) type=LOGIN_ERROR, realmId=master, clientId=null, userId=null, ipAddress=10.32.0.1, error=expired_code, restart_after_timeout=true
09:42:45,789 WARN [org.keycloak.events] (default task-4) type=LOGIN_ERROR, realmId=master, clientId=null, userId=null, ipAddress=10.32.0.1, error=expired_code, restart_after_timeout=true
09:42:45,907 WARN [org.keycloak.events] (default task-4) type=LOGIN_ERROR, realmId=master, clientId=null, userId=null, ipAddress=10.32.0.1, error=expired_code, restart_after_timeout=true
09:42:46,215 WARN [org.keycloak.events] (default task-4) type=LOGIN_ERROR, realmId=master, clientId=null, userId=null, ipAddress=10.32.0.1, error=expired_code, restart_after_timeout=true
09:42:46,336 WARN [org.keycloak.events] (default task-4) type=LOGIN_ERROR, realmId=master, clientId=null, userId=null, ipAddress=10.32.0.1, error=expired_code, restart_after_timeout=true
09:46:57,976 WARN [org.keycloak.events] (default task-5) type=LOGIN_ERROR, realmId=master, clientId=null, userId=null, ipAddress=10.32.0.1, error=expired_code, restart_after_timeout=true
09:46:58,137 WARN [org.keycloak.events] (default task-5) type=LOGIN_ERROR, realmId=master, clientId=null, userId=null, ipAddress=10.32.0.1, error=expired_code, restart_after_timeout=true
09:46:58,256 WARN [org.keycloak.events] (default task-5) type=LOGIN_ERROR, realmId=master, clientId=null, userId=null, ipAddress=10.32.0.1, error=expired_code, restart_after_timeout=true
09:46:58,375 WARN [org.keycloak.events] (default task-5) type=LOGIN_ERROR, realmId=master, clientId=null, userId=null, ipAddress=10.32.0.1, error=expired_code, restart_after_timeout=true
09:46:58,499 WARN [org.keycloak.events] (default task-5) type=LOGIN_ERROR, realmId=master, clientId=null, userId=null, ipAddress=10.32.0.1, error=expired_code, restart_after_timeout=true
09:46:58,931 WARN [org.keycloak.events] (default task-5) type=LOGIN_ERROR, realmId=master, clientId=null, userId=null, ipAddress=10.32.0.1, error=expired_code, restart_after_timeout=true
09:46:59,108 WARN [org.keycloak.events] (default task-5) type=LOGIN_ERROR, realmId=master, clientId=null, userId=null, ipAddress=10.32.0.1, error=expired_code, restart_after_timeout=true
extraEnv: |
- name: PROXY_ADDRESS_FORWARDING
value: "true"
But I am still having the same issue.