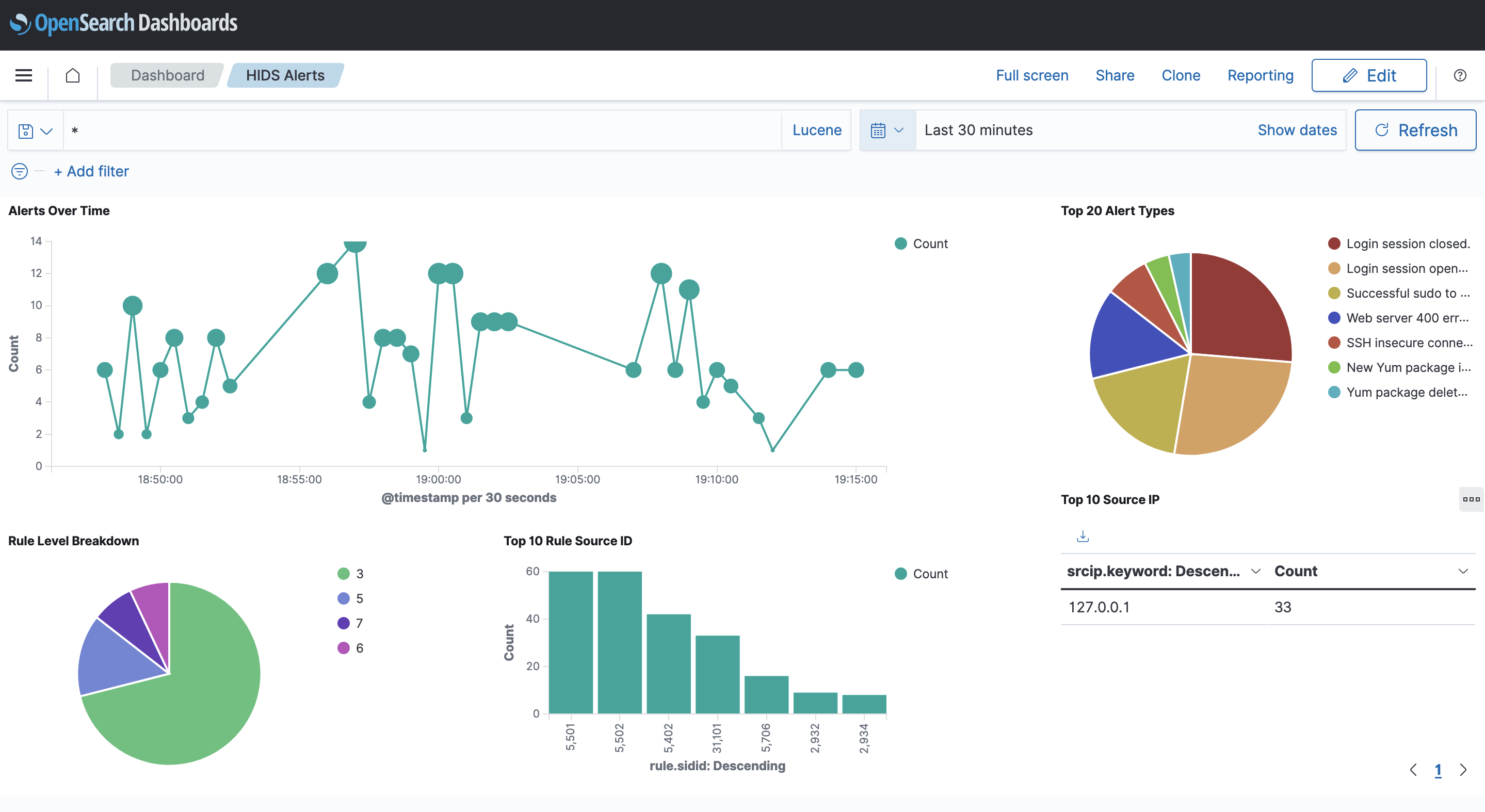
This solution uses Amazon CloudWatch Logs to collect and aggregate alerts in near real time from an open-source security (OSSEC) HIDS. It uses a CloudWatch Logs Subscription to deliver the alerts to Amazon OpenSearch Service for analysis and visualization with OpenSearch Dashboards.
This solution contains a test environment AWS CloudFormation stack that you can automatically provision into an existing Amazon VPC subnet. The CloudFormation template performs the following high-level steps in the region you choose:
- Creates two EC2 instances running Amazon Linux with an AWS Identity and Access Management (IAM) role for CloudWatch Logs access. Note: In order to provide sample HIDS alert data, the two EC2 instances are configured automatically to generate simulated HIDS alerts locally.
- Installs and configures OSSEC, the CloudWatch Logs agent, and additional packages used for the test environment.
- Creates the target HIDS Amazon OpenSearch domain.
- Creates the target HIDS CloudWatch Logs group.
- Creates the Lambda function and CloudWatch Logs Subscription in order to send HIDS alerts to Amazon OpenSearch.
- On the target EC2 instances, the OSSEC HIDS generates alerts that the CloudWatch Logs agent captures. The HIDS performs log analysis, integrity checking, Windows registry monitoring, rootkit detection, realtime alerting, and active response. For more information, see Getting started with OSSEC.
- The CloudWatch Logs group receives the alerts as events.
- A CloudWatch Logs subscription is applied to the target log group to forward the events through AWS Lambda to Amazon OpenSearch.
- Amazon OpenSearch loads the logged alert data.
- OpenSearch visualizes the alerts in near real time. OpenSearch Dashboards is an open-source visualization tool designed to work with OpenSearch. Amazon OpenSearch Service provides an installation of OpenSearch Dashboards with every OpenSearch Service domain.
For the following input parameters, you must identify a target VPC and subnet (which requires Internet access) for deployment. If the target subnet uses an Internet gateway, set the AssignPublicIP parameter to true. If the target subnet uses a NAT gateway, you can leave the default setting of AssignPublicIP as false.
You also must provide a trusted source IP address or CIDR block for access to the environment following the creation of the stack and an EC2 key pair to associate with the instances. You can find information about creating an EC2 key pair in the documentation here. Note that the trusted IP address or CIDR block also is used to create the access policy automatically for dashboard access. It is recommended that you utilize a specific IP address or CIDR range rather than using 0.0.0.0/0 which will allow all IPv4 addresses to access your instances.
- HIDSInstanceSize: EC2 instance size for test server
- OpenSearchInstanceSize: OpenSearch instance size In region S3 key for Lambda zipped deployment package
- VPCId: An Amazon VPC into which to deploy the solution
- SubnetId: A SubnetId with outbound connectivity within the VPC you selected (requires Internet access)
- AssignPublicIP: Set to true if your subnet is configured to connect through an Internet gateway; set to false if your subnet is configured to connect through a NAT gateway
- MyTrustedNetwork: Your trusted source IP or CIDR block that is used to whitelist access to the EC2 instances and the Amazon OpenSearch endpoint
If you already have a VPC Subnet configured with internet access, you can launch the stack using the CloudFormation Template.
Thanks to the OSSEC Project Team for authoring the OSSEC HIDS.